Zenmap is the official GUI for Nmap.
It aims to make Nmap easy for beginners to use while providing advanced features for experienced users.
- In it the frequently used scans can be saved as profiles to make them easy to run repeatedly.
- Saved scan results can be compared with one another. The results of recent scans are stored in a searchable database.
Note: Zenmap requires a good knowledge of Nmap options and their working.
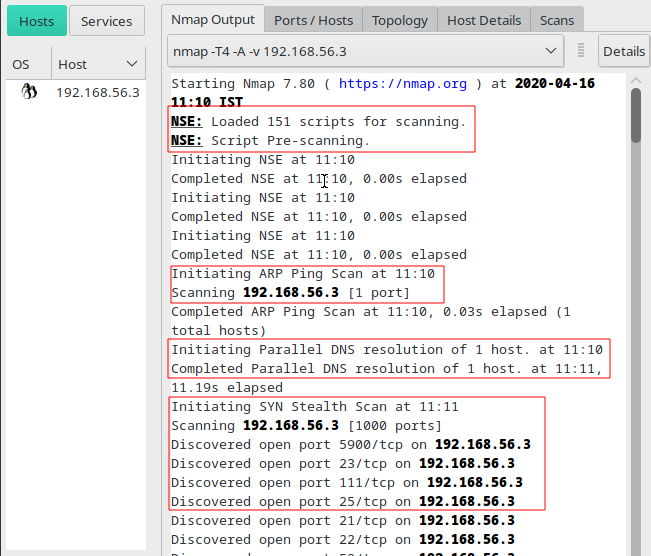
Intense scan on Metasploitable2 Using Zenmap
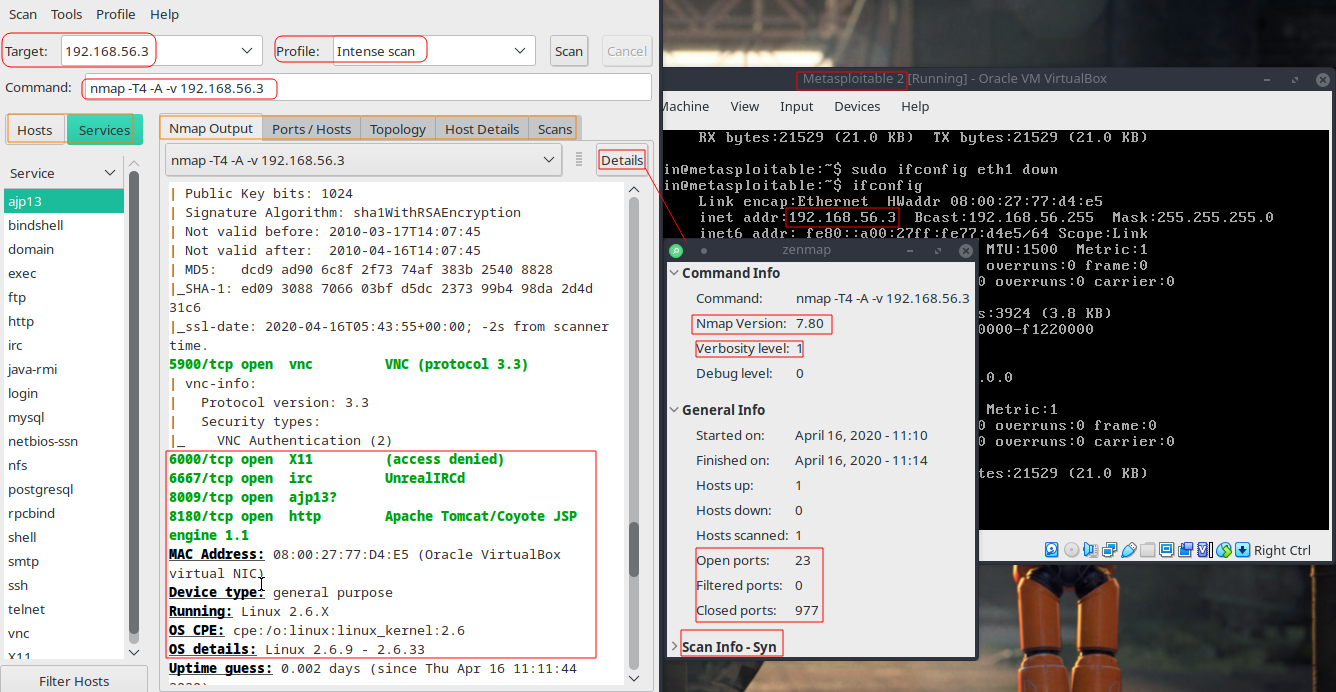
Scan Initilization
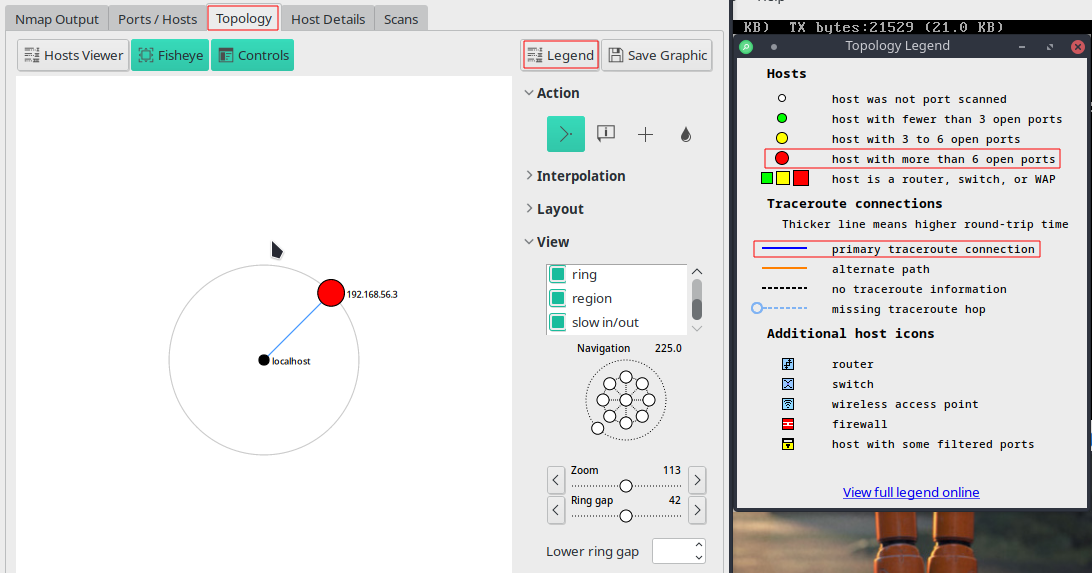
Topology
Commands used
- -T<0-5>:Set timing template (higher is faster)
Timing template in Nmap is used to optimize and improve the quality and performance of the scan to get desired results.
The templates:
- Paranoid mode (0),Sneaky mode (1) - These two are for IDS evasion.
- Polite mode (2) - It slows down the scan to use less bandwidth and less target machine resources.
- Normal mode (3) - It is the default mode and so '-T3' does nothing
- Aggressive mode (4) - It speeds scans up by making the assumption that you are on a reasonably fast and reliable network. It is the recommended mode. It sends packets very fast and waits 1.5 seconds for the response. The time difference between the two packets sent is up to 10 milliseconds.
- Insane mode (5) - It assumes that you are on an extraordinarily fast network or are willing to sacrifice some accuracy for speed. It sends packets insanely fast and waits only 0.3 seconds for the response. The time difference between the two packets sent is up to 5 milliseconds. This scan can cause network failiure.
- -A (Aggressive scan options):Enable OS detection, version detection, script scanning, and traceroute
- This option enables additional advanced and aggressive scan options:
OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (--traceroute) - This scan require root privileges because of options which require privileges (e.g. root access) such as OS detection and traceroute.
- Timing options (such as -T4) or verbosity options (-v) are not present in it.
- -sV -Helps in determinig the version of the protocol or service running on target to make it easier to search for an exploit.
- -sC -Performs a script scan using the default set of NSE scripts.
The Nmap Scripting Engine (NSE) is one of Nmap's most powerful and flexible features. It allows users to write (and share) simple scripts (in Lua) to automate a wide variety of networking tasks.
- Script scanning with the default set is considered intrusive,therefore do not use it without permission.
Nmap scripts can be used for:
- Vulnerability detection.
- Vulnerability exploitation.
- Backdoor detection.
- Network discovery.
- More sophisticated and accurate OS version detection.
There are many scripts present in the default option which can be found here.
To get help regarding a script use the following command:
sudo nmap --script-help [script name].nse
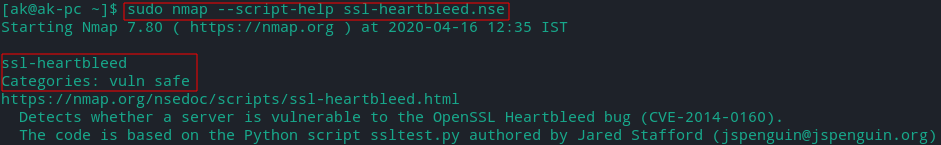
- -V (Increase verbosity level) :Print version number
- -vlevel (Set verbosity level) , level = 1,2,3
It increases the verbosity level, causing Nmap to print more information about the scan in progress. Open ports are shown as they are found and completion time estimates are provided when Nmap thinks a scan will take more than a few minutes. Use it twice or more for even greater verbosity.